IAM Overview
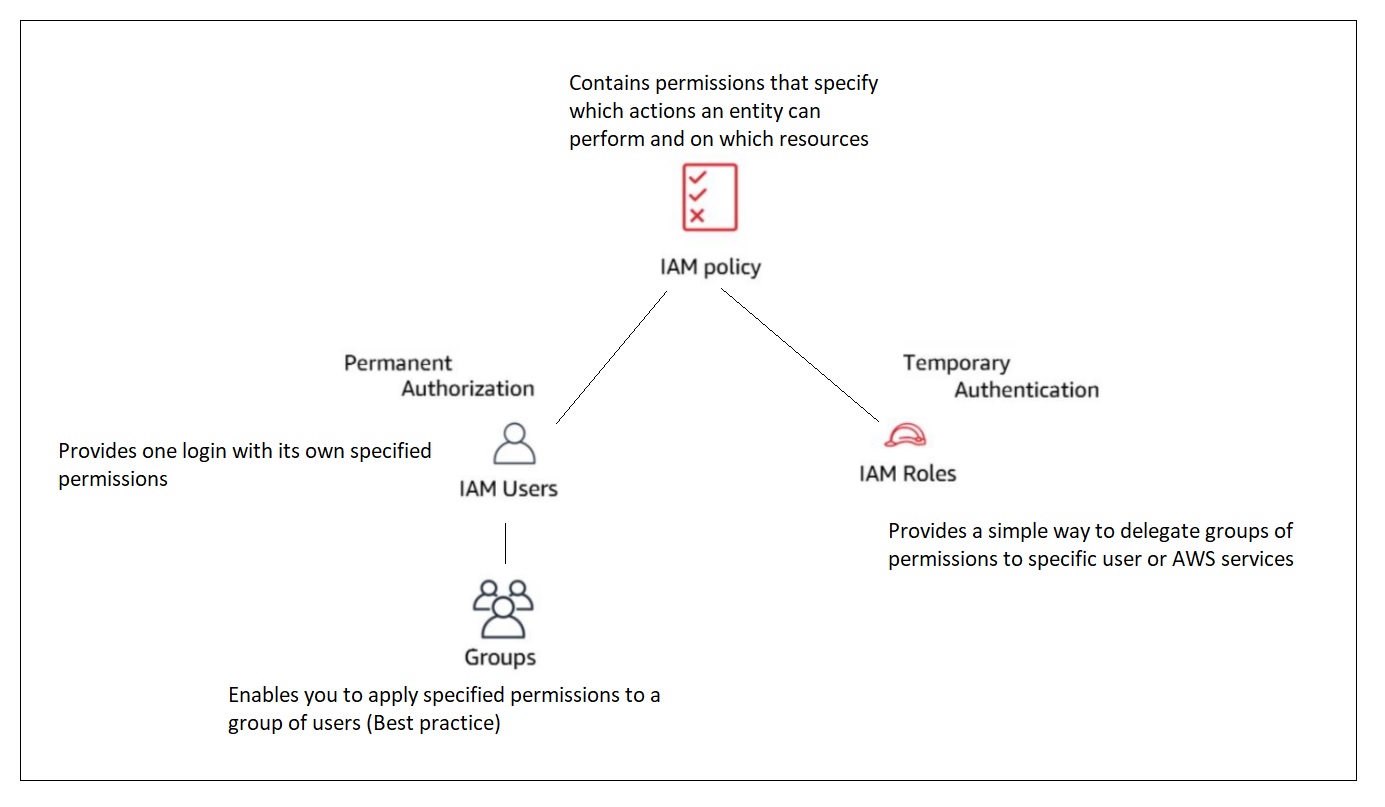
It is not reccomended to use the rootuser for any workloads/CLI/SDK access, rather setup a IAM users and grant access either by policy (single rule) or role. Think of a role as a hat that the user can wear to then have access to resources.
“An IAM role is an IAM identity that you can create in your account that has specific permissions. An IAM role is similar to an IAM user, in that it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS.”
“A role is intended to be assumable by anyone or thing who needs it.”
“An IAM role is similar to a user in that it is an AWS identity with permissions policies that determine what the identity can and cannot do in AWS. A role is intended to be assumable by anyone or thing who needs it. A role does not have standard long-term credentials (password or access keys) associated with it. Instead, if a user assumes a role, temporary security credentials are created dynamically and provided to the user.”
Prerequisites
To configure the below you will need the required access key id and secret access key which you can get from the AWS AMI Console (Identity and Access Management) you will need to be logged in. Any commands that point to a .json configuration file are available on github.
AWSCLI
Updated 05/03/2022
- Install using the CLI
This will live in C:\Program Files\Amazon\AWSCLI and should then work from any terminal.
- Check version
1 | aws --version |
This could show v1 or v2 - I had to uninstall v1 to get v2 to work, there may be a switcher as v2 have breaking changes.
1 | aws-cli/1.21.7 Python/3.6.0 Windows/10 botocore/1.22.7 |
- Configure with the keys you got from the IAM in the amazon console.
1 | C:\> aws configure |
This creates these text files in the following location:
%USERPROFILE%\.aws\credentials(windows)~/.aws/credentials(linux)
1 | ~ C:\Users\[USERNAME]\.aws\credentials |
%USERPROFILE%\.aws\config(windows)~/.aws/config(linux)
1 | ~ C:\Users\[USERNAME]\.aws\config |
- Then you can test it works
1 | aws iam list-roles |
- Create the task execution IAM role
1 | --- Create the task execution role |
More than one profile
As I have more than one profile I use --profile carlos this means my default profile is not used
config
1 | [default] |
credentials
1 | [default] |
References
- https://docs.aws.amazon.com/sdk-for-net/latest/developer-guide/creds-file.html
- https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html#create-iam-users
- https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies.html
- https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles.html
- https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_aws-services-that-work-with-iam.html
ECSCLI (Elastic Container Service)
This will live in C:\Program Files\Amazon\ECSCLI
- Run windows powersell as administrator
1 | --- create folder |
Edit the environment variables and add
C:\Program Files\Amazon\ECSCLIto thePATHvariable fieldRestart powersell and check version
1 | ecs-cli --version |
- Configure with the same keys used above
I used the profile names carl_ecs_cli_profile and carl_configuration_name below when setting up ECS for the Lexicon via the AWS CLI.
1 | ecs-cli configure profile --profile-name carl_ecs_cli_profile --access-key HOEHOEHOEHOHEOHEOHE --secret-key HO/hehOehoHEOHEhohEOHeohEOH+EohOEe |
Note that --cluster needs to satisfy regular expression pattern: [a-zA-Z][-a-zA-Z0-9]*
This creates these files which you can edit with any text editor.
1 | ~ C:\Users\[USERNAME]\AppData\Local\ecs\config |
References
- https://docs.aws.amazon.com/cli/latest/userguide/install-windows.html#install-msi-on-windows
- https://docs.aws.amazon.com/AmazonECS/latest/developerguide/ECS_CLI_installation.html
- https://docs.aws.amazon.com/AmazonECS/latest/developerguide/ECS_CLI_Configuration.html
- https://console.aws.amazon.com/iam/
- https://docs.aws.amazon.com/toolkit-for-visual-studio/latest/user-guide/tkv-create-ami-from-instance.html