Errors related to Deploying .NET Applications To Azure
Errors
ContainerAppRegistryInUse
1 | Error: updating Container App (Subscription: "00000000-0000-0000-0000-000000000002" |
Deactivate revision
1 | az containerapp revision deactivate --revision demo-aca-bb8c7a39-dev--os0hfry --resource-group demo-rg-bb8c7a39-dev |
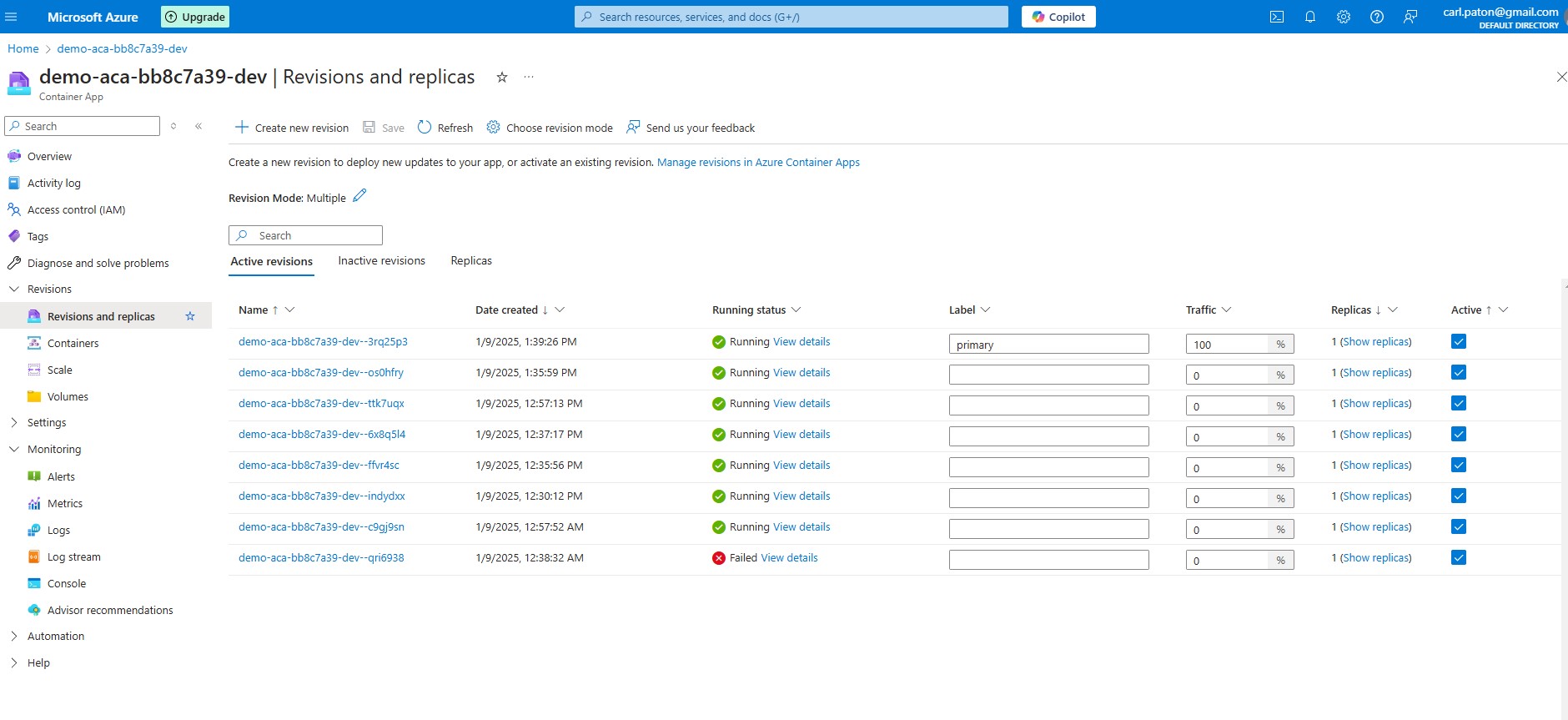
Also check if you actuall need revision_mode=Multiple
MissingSubscriptionRegistration
While trying to add azurerm_container_app_environment it shat the bed
1 | azurerm_container_app_environment.demo-cae: Creating... |
Here https://aka.ms/rps-not-found helped us out and showed the commands to run.
- Query the provide
1 | az provider list --query "[?namespace=='Microsoft.App']" --output table |
Should output: NotRegistered
1 | Namespace RegistrationState RegistrationPolicy |
- Register which should output
Registering is still on-going. You can monitor using 'az provider show -n Microsoft.App'
1 | az provider register --namespace Microsoft.App |
- Check the status
1 | az provider list --query "[?namespace=='Microsoft.App']" --output table |
Registering
1 | Namespace RegistrationState RegistrationPolicy |
Registered
1 | Namespace RegistrationState RegistrationPolicy |
AuthorizationFailed - Error retrieving keys for Storage Account
Errors when trying use storage for the tfstate
1 | │ Error: Failed to get existing workspaces: Error retrieving keys for Storage Account "demoiacbb8c7a39": storage.AccountsClient#ListKeys: Failure responding to request: StatusCode=403 -- Original Error: autorest/azure: Service returned an error. Status=403 Code="AuthorizationFailed" Message="The client '00000000-0000-0000-0000-000000000003' with object id '00000000-0000-0000-0000-000000000003' does not have authorization to perform action 'Microsoft.Storage/storageAccounts/listKeys/action' over scope '/subscriptions/***/resourceGroups/reference-rg/providers/Microsoft.Storage/storageAccounts/demoiacbb8c7a39' or the scope is invalid. If access was recently granted, please refresh your credentials." |
We need to apply a role to this client
1 | az role assignment create --assignee 00000000-0000-0000-0000-000000000003 --role Contributor --scope /subscriptions/00000000-0000-0000-0000-000000000002 |
AuthorizationFailed - Error creating RBCA from AZ CLI
When trying to run az ad sp create-for-rbac it shat the bed
1 | (AuthorizationFailed) The client 'name.surname.admin@domain.co.nz' with object id '00000000-0000-0000-0000-000000000001' does not have authorization to perform action 'Microsoft.Authorization/roleAssignments/write' over scope '/subscriptions/00000000-0000-0000-0000-000000000002/resourceGroups/my-uat-rg/providers/Microsoft.Authorization/roleAssignments/00000000-0000-0000-0000-000000000003' or the scope is invalid. If access was recently granted, please refresh your credentials. |
00000000-0000-0000-0000-000000000001 is the id for the user I login with obfuscated as name.surname.admin@domain.co.nz.
On the subscription, I needed to add role User Access Administrator for my user ‘name.surname.admin@domain.co.nz‘