Using ASP.NET I needed a way to identify users by role, these users are managed by Entra ID, the roles are configured in Entra under the registered application and the assigned to the user.
These steps assume you already have an Entra ID and an application registered with Entra, I didnt use the Entra UI but rather Visual Studio Connected Services
Entra UI Steps
MS will probably update their UI tomorrow but these steps are correct as of 15/01/2025
Create User
- Log into https://entra.microsoft.com/
- On the left select
Users->All Users->+ New User->Crate new user - Populate the required fields, these are values referenced below in this post
1 | User principal name: carl.test |
- Dont add any groups/roles here, just create
Create Roles
- Log into https://entra.microsoft.com/
- On the left select
Applications->App registrations-> select the owned application instance - On the left select
App roles->+ Create app role - Populate the details as follows, the
Valueis what will be checked for in the code
1 | Display name | Allowed member types | Value | Description |
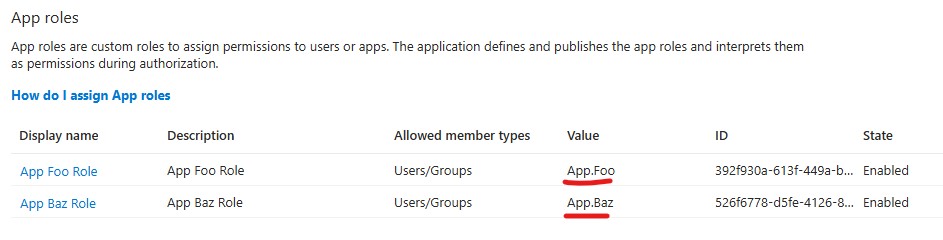
- Select
Overview->Managed application in local directory(its near the top right) - On the left select
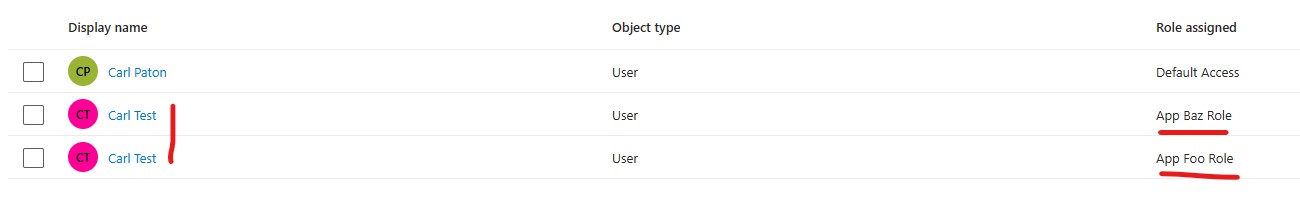
Users and groups->+ Add user/group - Users -> click
None Selected-> Check next toCarl Testand clickSelect - Select a role -> click
None Selected-> clickApp Foo Roleand clickAssign - Repeat for other roles like
App Baz Role
Code Steps (Auth Policy)
Simliar to Auth Policy Checking Scope we can create Policies based claims
- In
program.csbuild the policy
1 | builder.Services.AddAuthorizationBuilder() |
- In the controller add the annotation
1 | [] |
Alternatively just check for the Role directly
1 | [] |
Code Steps (Logic by Role)
We can confirm all the users claims by checking the context
- Register the ContextAccessor In
program.cs
1 | builder.Services.AddHttpContextAccessor(); |
- Inject
IHttpContextAccessorand query all claims
1 | public HomeController(ILogger<HomeController> logger, IHttpContextAccessor httpContextAccessor) |
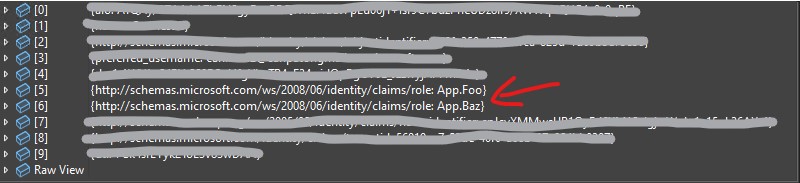
- This will give a key value of all claims, the ones we care about are
App.FooandApp.Baz. In this case the claim is a role.
- You can then build a service that instead takes
IHttpContextAccessorand returns true/false by role using IsInRole.
This can then programatically show/hide parts of the application or dictate logical flow.
1 | public class RoleService(IHttpContextAccessor httpContextAccessor) |
Code Steps (Logic by Group)
This can also be done with groups using the same policy approach as above with RequireClaim
1 | builder.Services.AddAuthorization(o => |
You get the group GUID from Entra and assign it the user.
References
- https://learn.microsoft.com/en-us/aspnet/core/security/authorization/roles
- https://learn.microsoft.com/en-us/aspnet/core/security/authorization/claims
- https://learn.microsoft.com/en-us/entra/identity-platform/howto-add-app-roles-in-apps
- https://learn.microsoft.com/en-us/entra/identity-platform/access-token-claims-reference
- https://www.youtube.com/watch?v=Sc1y4WBHP2k