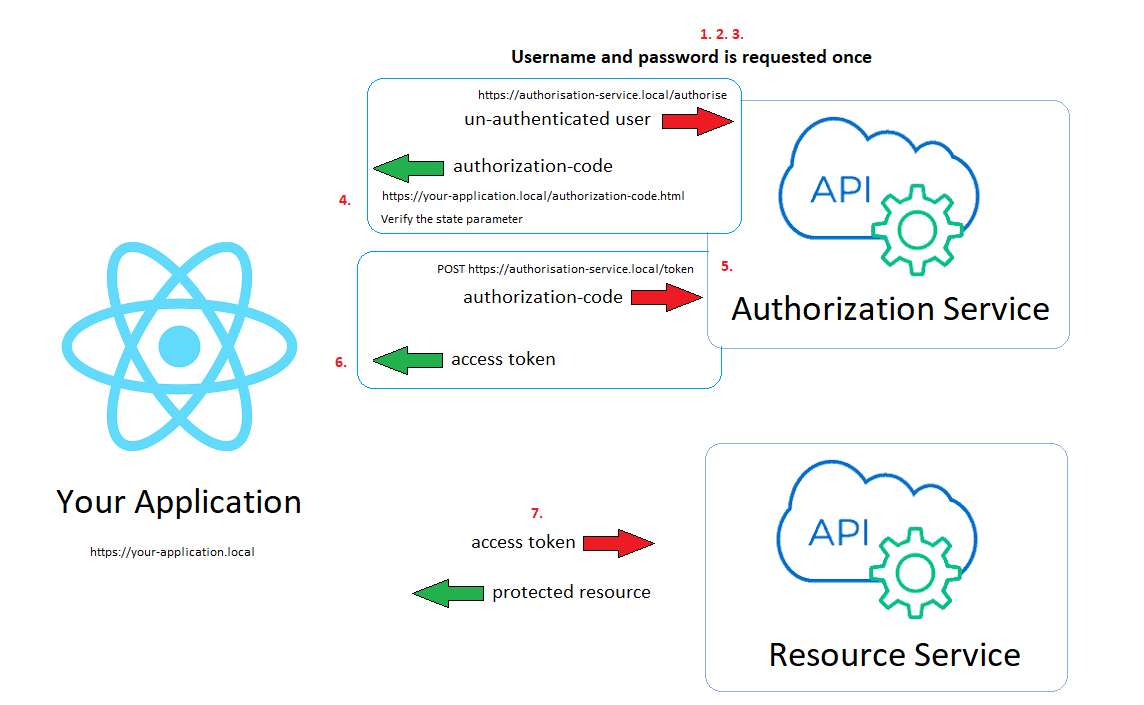
Grant Type - Authorization Code Flow, steps 1->7 are explained below.
The flows below assume you have registered the client (your application) and created a user. Typically registration involves a developer account at the service, answering questions about your application, uploading a logo etc.
The user is the single sign on (SSO) account. This could be Google, Facebook, Active Directory ect.
All the tokens and secrets below are overly simplified.
Flow
The user opens your application at
https://your-application.localand is not authenticated.Your application builds an authorization URL and redirect to the authorization service at
https://authorisation-service.local
client_idis your application id that is registered with the authorization serviceredirect_uriis the landing page on your application where the now authenticated user will be redirected to along with theauthorization-codescopeis used for the resource accessstateis a random string
1 | https://authorisation-service.local/authorise? |
The user then provides the authorization service their USERNAME and PASSWORD, it then validates the users credentials.
The username/password are never given back to your application. The user is then redirected back to your application based on
redirect_uriwith query parametersstateandcode. You must then verify the state parameter is what you passed above, so18b1abb9830d=18b1abb9830dto protect against Cross Site Request Forgery (CSRF) attacks.
1 | https://your-application.local/authorization-code.html? |
- The authorization code is then programatically sent back to
https://authorisation-service.local/tokenwith a POST request to exchange it for an access token. This POST includes yourclient_secret
- Its considered best practice to to include the
Proof Key for Code Exchange(PKCE) flow here (pronounced “pixy”) - You just need to provide a
client_secretauthorization code. client_secretwould have been provided when the client was registered.
“The key difference between the PKCE flow and the standard Authorization Code flow is users aren’t required to provide a client_secret. PKCE reduces security risks for native apps, as embedded secrets aren’t required in source code, which limits exposure to reverse engineering.” - developers.onelogin.com
1 | POST https://authorisation-service.local/token |
- The response could look like
1 | { |
- Resource requests then need to include the
token_typeandaccess_tokenin the authorisation header. Note the American spelling with az.
1 | 'Authorization':'Bearer eaabf941fbd1' |