In cryptography, a salt is random data that is used as an additional input to a one-way function that “hashes” data, a password or passphrase. Salts are closely related to the concept of nonce. The primary function of salts is to defend against dictionary attacks or against its hashed equivalent, a pre-computed rainbow table attack.
This can be visually demonstrated as:
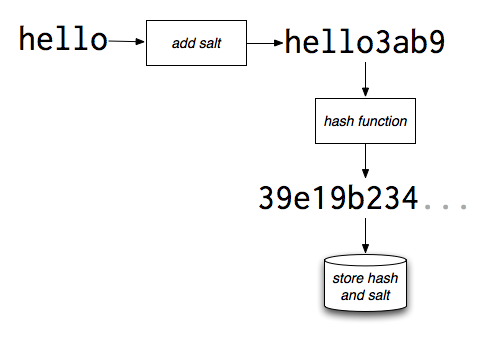
Cool, how do we do this in code?
Updated 24/04/2022
HMACSHA512
The salt string can be passed as the users email if you are lazy but its better to generate your own byte array.
1 | public class EncryptionService |
MD5
MD5 is considered deprecated
Consider the following username and password:
1 | var email = "foo@domain.com"; |
The password value needs to be hashed and then persisted to the database.
- Create the salt by getting the byte array values of the email, the assumption would be that an email address is unique.
You can SHOULD create a random byte array for the salt using RNGCryptoServiceProvider. You would then need to persist that byte array to the database and use it in your user authentication challenge routine. The use of email here is just a dirty example.
1 | var salt = Encoding.ASCII.GetBytes(email); |
- Create a byte array of the password and concatenate the two into one byte array
1 | var value = Encoding.UTF8.GetBytes(password); |
- Create a MD5 hash from the ‘salted value’
1 | // need MD5 to calculate the hash |
- Encode and to string the hash. You can also use
Convert.ToBase64String(hashedBytes);
1 | // string representation (similar to UNIX format) |
This would then result in a value of A9419D55933FBCF43BA46087F8F20B22